Business email security depends on proper domain authentication.
SPF, DKIM, and DMARC are the controls that prevent spoofing, phishing, and brand impersonation for Malaysian business domains.
Without these controls, attackers can send emails that appear to come from your company without triggering spam filters. Before configuring anything, it is important to understand what email authentication actually protects at a business level.
What Is Email Authentication and What Does It Actually Protect?
Email authentication verifies that emails are genuinely sent by systems authorized by the domain owner.
From a business perspective, email authentication protects three things:
- Brand trust – prevents attackers from impersonating your company name
- Customer and partner communications – reduces phishing and invoice fraud
- Email deliverability – ensures legitimate emails are not rejected or flagged as spam
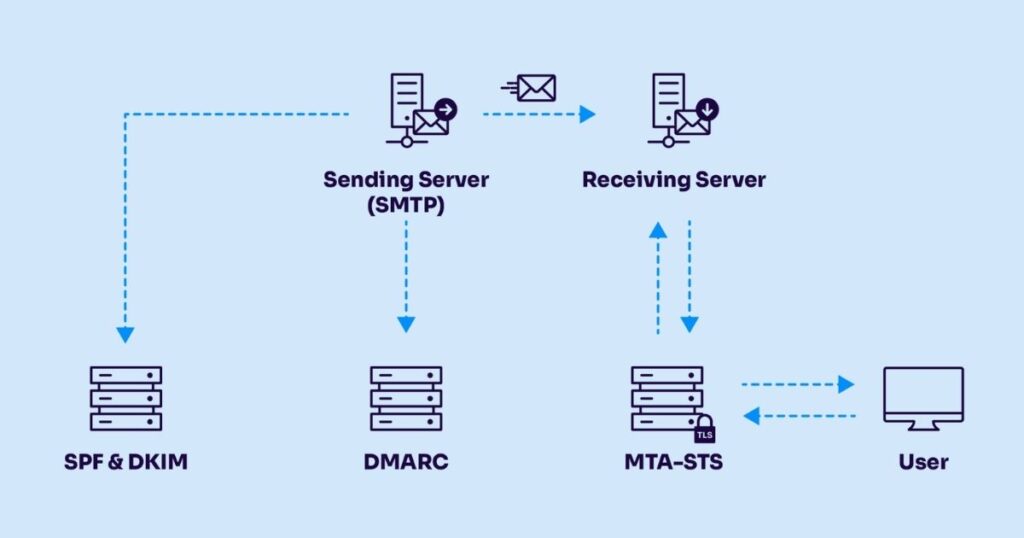
Email authentication is not a single tool. It is a system made up of three controls, each with a distinct role:
- SPF controls who is allowed to send emails for your domain
- DKIM protects what is inside the email by verifying message integrity
- DMARC enforces policy and provides visibility when authentication fails
The first layer of this system focuses on a basic question: Which servers are allowed to send emails on behalf of your domain.
What Is SPF and How Does It Control Who Can Send Emails for Your Domain?
SPF (Sender Policy Framework) defines which mail servers are allowed to send emails on behalf of your domain.
SPF works by publishing a DNS record that lists authorized sending sources. When an email is received, the recipient’s mail server checks this record to verify whether the sending server is permitted. If the server is not authorized, the email can be rejected or flagged.
For Malaysian businesses, SPF typically covers multiple systems, including:
- Microsoft 365 or Google Workspace
- Accounting and invoicing platforms
- HR and payroll systems
- CRM and marketing tools
SPF is effective at blocking unauthorized senders, but it is also commonly misconfigured. Typical SPF issues include missing third-party services, multiple SPF records on the same domain, or exceeding DNS lookup limits. When this happens, legitimate business emails may fail authentication.
While SPF controls where emails come from, it does not verify whether the email itself was altered after it was sent. That responsibility belongs to the next layer: DKIM, which protects email integrity.
What Is DKIM and How Does It Protect Email Integrity?
DKIM (DomainKeys Identified Mail) verifies that an email has not been modified after it is sent.
DKIM works by digitally signing outgoing emails using a cryptographic key published in your domain’s DNS records. When the email reaches the recipient’s mail server, that signature is checked to confirm the message content has not been altered in transit.
For businesses, DKIM is especially important for emails that carry sensitive or high-trust information, such as:
- Invoices and payment instructions
- Contracts and legal documents
- HR, payroll, and internal management communications
Without DKIM, an email may still appear to come from an authorized server, but there is no guarantee that its contents were not tampered with. This creates risk for invoice fraud and message manipulation, even when SPF is in place.
Common DKIM issues include incorrect selector records, missing DKIM on subdomains, or incomplete deployment across different email-sending platforms. These gaps weaken email authentication and can affect both security and deliverability.
SPF and DKIM validate senders and message integrity, but they do not define what should happen when validation fails. That enforcement role belongs to DMARC.
What Is DMARC and How Does It Enforce Email Security Policies?
DMARC (Domain-based Message Authentication, Reporting, and Conformance) defines how receiving servers should handle emails that fail SPF or DKIM checks.
DMARC works by aligning SPF and DKIM results and applying a clear policy. This policy tells receiving mail servers whether to:
- Monitor failed emails without taking action
- Quarantine suspicious emails
- Reject unauthenticated emails entirely
In addition to enforcement, DMARC provides reporting. These reports show which systems are sending emails on behalf of your domain and whether those emails are passing or failing authentication checks. This visibility is critical for identifying unknown senders, misconfigured systems, or attempted impersonation.
For Malaysian businesses, DMARC plays a key role in protecting brand identity. Without it, attackers can spoof company domains to target customers, suppliers, or internal staff – often without being detected.
When properly configured, DMARC turns SPF and DKIM from passive checks into an enforceable email security policy. Together, these three controls form a single authentication system that protects business communications from abuse.
How SPF, DKIM, and DMARC Work Together
SPF, DKIM, and DMARC work together as a layered email authentication system.
| Control | What It Checks | What It Does | Business Value |
|---|---|---|---|
| SPF | Sending server | Verifies authorized senders | Prevents spoofed sender domains |
| DKIM | Message integrity | Authenticates email content | Protects invoices and contracts |
| DMARC | Policy alignment | Enforces action and reporting | Visibility and enforcement |
Individually, each control addresses a specific risk. Together, they provide sender validation, message integrity, and policy enforcement across all business email communications.
Because these controls interact with each other and depend on DNS configuration, they require ongoing oversight rather than a one-time setup.
How Email Authentication Fits into Ongoing IT Management?
Email authentication is not a one-time setup. It requires continuous monitoring, policy management, and coordination across systems.
As businesses adopt new SaaS platforms, change vendors, or introduce additional email-sending tools, SPF, DKIM, and DMARC records must be reviewed and updated. Without this oversight, legitimate systems may fail authentication, or worse, unauthorized senders may go unnoticed.
In practice, email authentication sits alongside broader responsibilities such as server configuration, DNS management, security monitoring, and access control. Treating SPF, DKIM, and DMARC as part of ongoing IT management and security governance helps ensure these controls remain effective as the environment changes. This is typically handled within a structured IT management framework that covers system upkeep, monitoring, and policy enforcement across the organization.
Wrapping Up: Email Security Depends on Visibility and Control
SPF, DKIM, and DMARC protect the integrity of business email by ensuring messages come from authorized systems, remain unaltered, and follow clear enforcement policies.
When properly configured, these controls reduce spoofing, phishing, and impersonation risks. More importantly, they provide visibility into how a business domain is being used across email systems.
Email security is not about adding more tools. It is about maintaining control over who can communicate on behalf of your business and ensuring that trust is preserved as systems, vendors, and workflows evolve.




